Protect sensitive information seamlessly
$31.77/year
Proofpoint Email Data Loss Prevention provides a comprehensive solution designed to protect sensitive data in emails and prevent data loss. Our platform identifies and classifies critical information, ensuring compliance with regulations while minimizing the risk of breaches. By implementing dynamic encryption policies, we secure communications between internal users and external partners. With advanced detection capabilities, our solution scans various file types and employs sophisticated algorithms to accurately identify sensitive content. This proactive approach not only enhances data security but also streamlines management through a centralized dashboard, enabling organizations to respond swiftly to potential threats.
Top Features
Manage and enforce email DLP and encryption centrally on Proofpoint’s industry leading email gateway
Detect and analyze sensitive data in email messages and attachments
Integrate with Proofpoint Information Protection to comprehensively address the entire spectrum of human-centric data loss use cases
Recommended products
Identify data unique to your organization
Email DLP and Encryption identifies data unique to your organization. It comes with hundreds of proven prebuilt data identifiers and dictionaries. These include financial services account numbers, local forms of ID and medical record numbers. You can also easily upload or create custom dictionaries or identifiers that are unique to your organization, as well as fine tune the matching strength of dictionary terms and exceptions. This allows you to analyze the email data that matters most to your organization.
Deep analysis and fingerprinting
Email DLP and Encryption accurately detects sensitive data within unstructured content. More than 300 file types can be scanned out of the box. The solution ensures that sensitive data located beyond standard Microsoft Office 365 and PDF attachments is properly handled. You can also use the filetype profiler to extend support to new, custom or proprietary file types, such as patents and memos.
Sensitive documents are fingerprinted—with both full and partial matching capabilities—even if the data resides in different file formats. You can also employ advanced methods for content-matching and text extraction from images. This includes index document matching, exact data matching and optical character recognition (OCR).

Automate regulatory compliance
Email DLP and Encryption automatically looks for all standard forms of restricted content. It quickly detects sensitive data with its prebuilt dictionaries. With detailed algorithmic checks built into smart identifiers, it minimizes false positives for credit card numbers and a wide variety of sensitive information. Advanced proximity and correlation analysis enhances detection analysis. The solution enables organizations to comply with PCI, SOX, GDPR, PII, HIPAA and more.
Real-time reporting
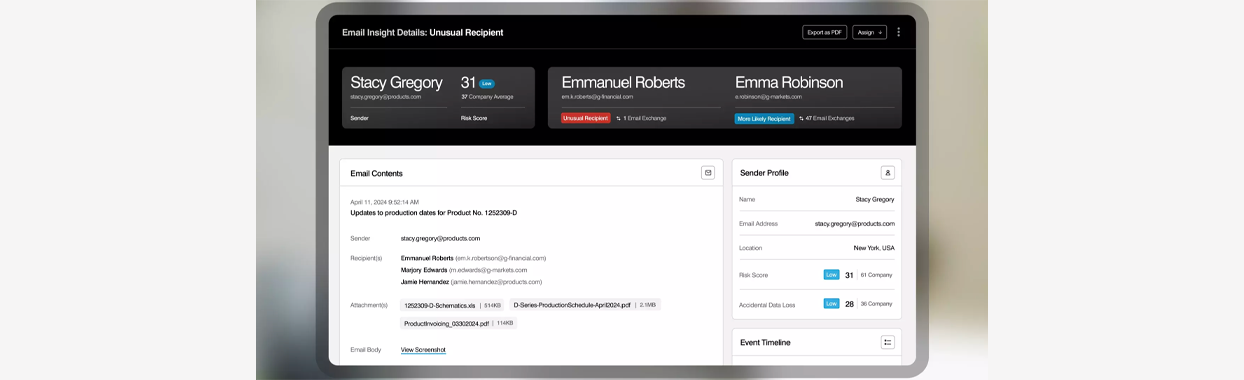
Email DLP and Encryption provides the visibility and workflow to help you make quick decisions and take action. It lets you see real-time statistics and trends as well as manage current incidents. You can also take appropriate actions on non-compliant messages. You can do all of this from a centralized dashboard. And you can drill down into any incident for review. A side-by-side highlighted view of regions of an email or attachment shows the matches next to the original document or policy. You can comment on, track and search violations in the incident manager. You can also export matching messages.
Improve operational effectiveness
Email DLP is part of our enterprise DLP approach. This allows you to find, track and safeguard data as users work in email, cloud applications and endpoints. It combines content, behavior and threat telemetry from these channels, which lets you address the full spectrum of human-centric data-loss scenarios through a unified alert management system. And you can easily apply common data detectors to deploy consistent DLP policies across channels. This helps save time and eliminates administrative headaches.
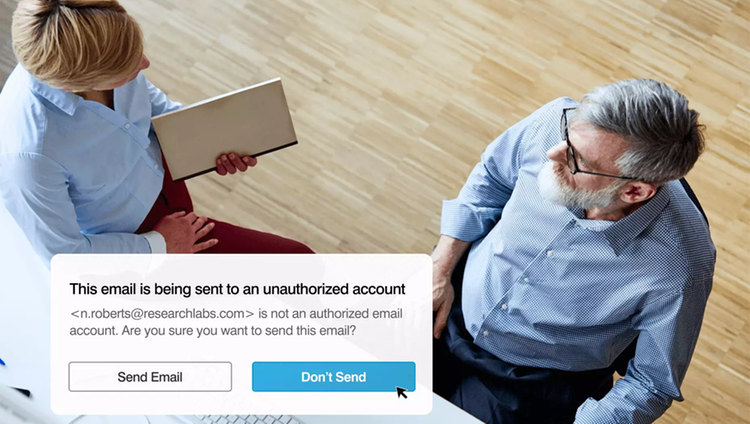
Routing policies like Smart Send make life easier for your DLP analysts. Emails can be sent back to the sender for self-remediation of outbound policy violations, or routed elsewhere—such as to HR, IT or business owner—as part of the workflow.

Assured encryption, visibility and controls
Email DLP and Encryption keeps your business communications flowing securely. It secures external or internal-to-internal communication with a robust set of controls and no-touch key management. Enabled by a policy-based DLP engine, the solution lets you define and dynamically apply granular encryption policies at the global, group and user levels with integrations with LDAP and Active Directory.
You can automate encryption by destination (that is, business partner, supplier), sender or message attributes such as attachment types. Or you can enable users to selectively apply encryption. Email encryption also serves as a TLS fallback to ensure fail-safe encryption. Recipients have flexible options to access encrypted messages, including a web portal, mobile browser or Outlook client.
For seamless, secure communication with business partners who also use Proofpoint Email DLP and Encryption, our Trusted Partner Encryption provides a transparent user experience for your end users. Messages are encrypted by the sending gateway. And the business partner’s Proofpoint gateway can automatically decrypt them before they are delivered to the internal email infrastructure.
Enhanced recipient experience
By providing a seamless user experience, Proofpoint Email DLP and Encryption prevents employees from working around the policies.

Expertise shortens time to value
Preventing data loss is not easy. It requires more than technical and product knowledge. It also requires a deep understanding of program objectives, data governance and data stewardship. We can be a trusted partner on your journey to ensure the success of your DLP program. Our managed service provides you with expertise that can help you optimize your technology investment, support your continuous operations and mature your data protection strategy
Additional Information
Terms & Conditions
Terms of Service
https://www.proofpoint.com/us/legal/licensePrivacy Policy
https://www.proofpoint.com/us/legal/privacy-policyResources
Proofpoint Email Data Loss Prevention - Solution Brief
PFPT Email DLP - S
PFPT-M-DLP-S-A$31.77 Unit / Year
For 1-500 Units
$19.97 Unit / Year
For 500-750 Units
$16.34 Unit / Year
For 750-1000 Units
$12.71 Unit / Year
For 1000-2500 Units
$11.80 Unit / Year
For 2500-5000 Units
$63.54 Unit / Year
For 1-500 Units
$39.94 Unit / Year
For 500-750 Units
$32.68 Unit / Year
For 750-1000 Units
$25.42 Unit / Year
For 1000-2500 Units
$23.60 Unit / Year
For 2500-5000 Units
$95.31 Unit / Year
For 1-500 Units
$59.91 Unit / Year
For 500-750 Units
$49.02 Unit / Year
For 750-1000 Units
$38.14 Unit / Year
For 1000-2500 Units
$35.40 Unit / Year
For 2500-5000 Units