Identify & redact sensitive data in APM, RUM and events stream
$0.45/month
Datadog's Sensitive Data Scanner is a tool designed to help organizations identify and manage sensitive data within their telemetry data, ensuring compliance with data protection standards. We offer predefined rules to detect various types of sensitive information like credit card numbers, email addresses, IP addresses, and API keys. Users can also create custom regex-based scanning rules to identify business-specific sensitive data. We allow for the management of sensitive data issues in logs, APM traces, and RUM events, facilitating triage, troubleshooting, and tracking of remediation tasks. We provide a centralized interface for discovering, triaging, and resolving data compliance issues efficiently.
Top Features
Configure Sensitive Data Scanner to build a scalable and holistic compliance strategy
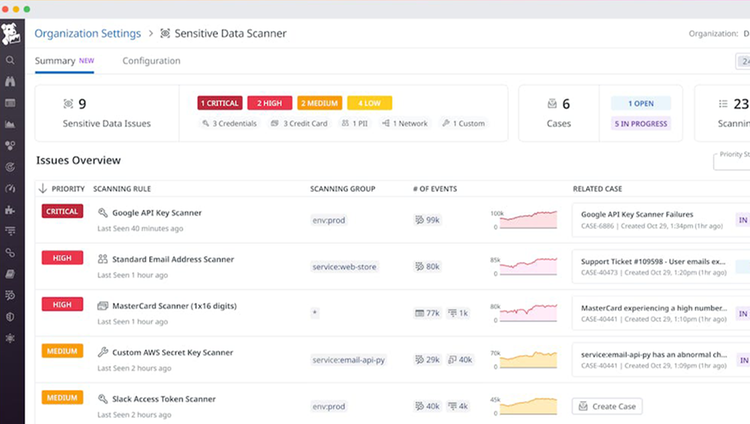
Classify sensitive data based on its content, source, or designated risk level
Redact sensitive data from security breaches and both insider and external threat actors
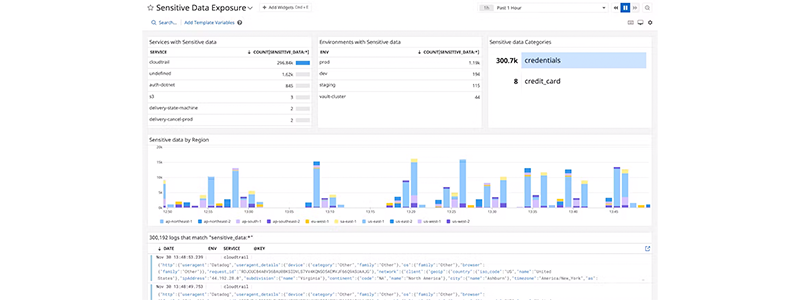
Discover sensitive data across your cloud environments
Recommended products
Configure Sensitive Data Scanner to build a scalable and holistic compliance strategy
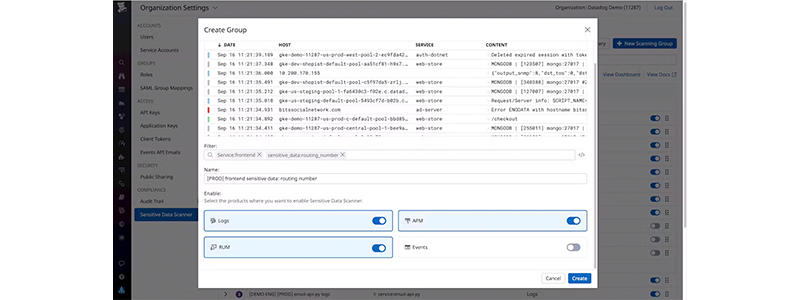
- Define exactly which data you want to scan using filters..
- Enable scanning for Log Management, APM, and RUM with a single click..
- Scan your data in real-time at ingestion to prevent data leaks.
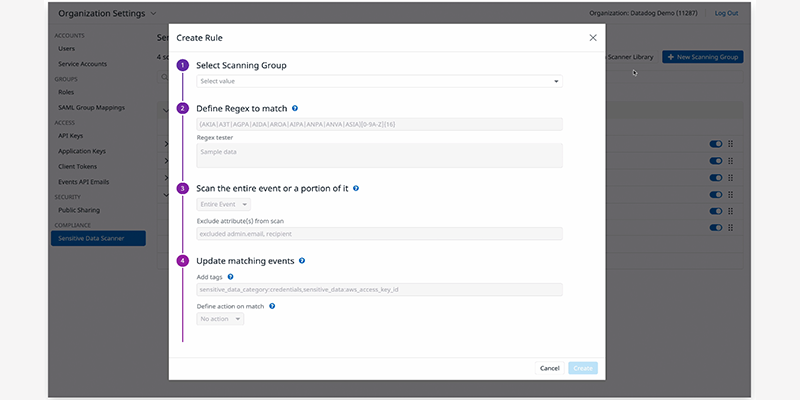
Classify sensitive data based on its content, source, or designated risk level
- Standardize data classification across dev, ops, and security teams and across different cloud platforms and hybrid environments..
- Accelerate classification through out-of-the-box rules that capture common patterns, such as credit card numbers, API keys, tokens, AWS secret keys, and others..
- Inform data governance policies with searchable tags on risk level, data source and priority about your company’s management of sensitive private data.
Discover sensitive data across your cloud environments
- Save time by scanning and tagging of new hosts, containers, and applications as soon as they are spun up..
- Tag sensitive data to allow teams to create real-time alerts and build dashboards..
- Reduce false positives with the help of industry-standard detection techniques, such as the Luhn algorithm..
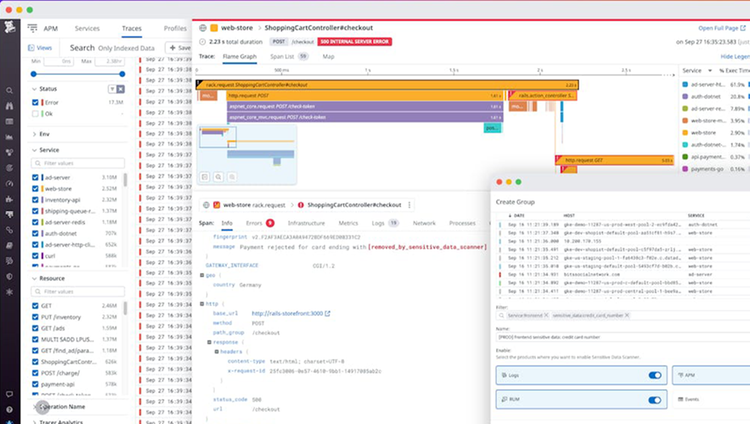
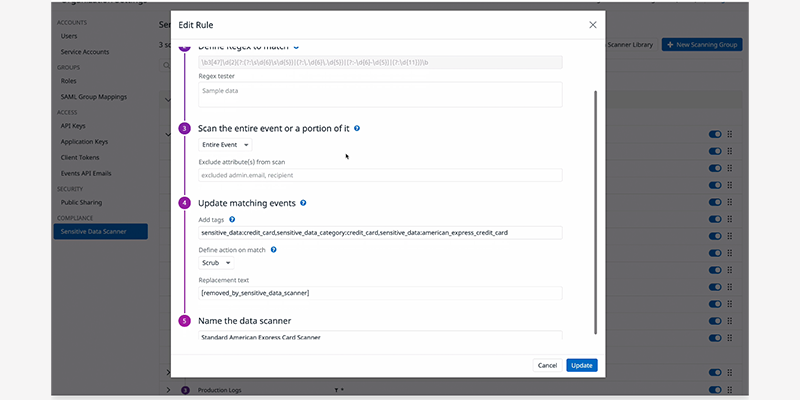
Redact sensitive data from security breaches and both insider and external threat actors
- Scrub sensitive data with predefined scanners from Datadog’s Data Scanner Library or custom scanners..
- Build a modern compliance strategy by combining sensitive data scanning with..
- Datadog’s fully integrated role-based access control (RBAC) permissions and restriction queries..
- Use audit logs to keep a full record of user activity on the Datadog platform.
Additional Information
Terms & Conditions
Terms of Service
https://www.datadoghq.com/legal/terms/Privacy Policy
https://www.datadoghq.com/legal/privacy/