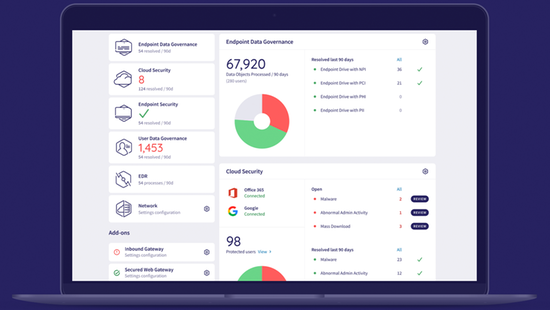
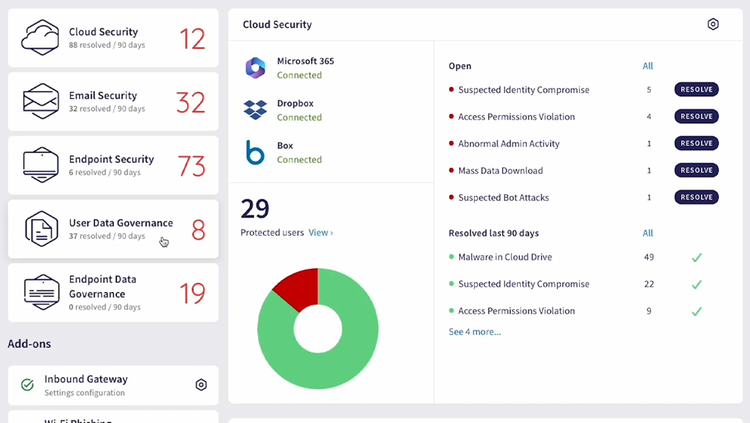
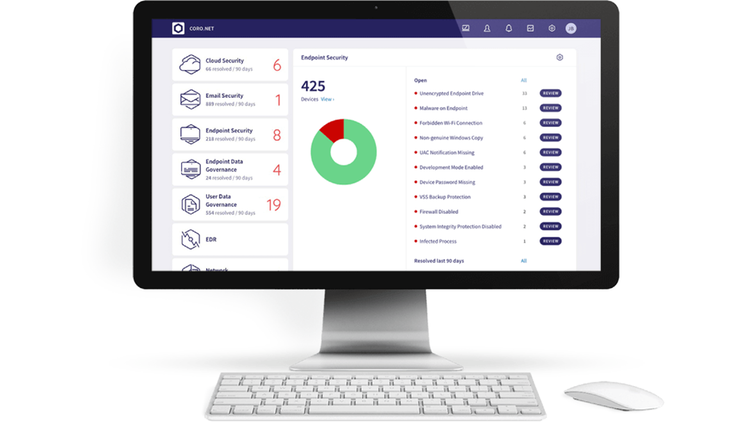
A single platform that secures your entire company
Traditional security applications are vector-specific, forcing businesses to adopt multiple security tools and advanced management systems to handle a dispersed stack. Unlike these dated solutions, Coro’s single-touchpoint platform houses a selection of security modules that work independently and in tandem and eliminate the need for multiple security tools and systems. Our modular security platform is the ultimate alternative to expensive, tech-heavy security solutions, uniquely designed for lean IT teams.
Top Features
Unified everything
Unlimited monitoring of endpoint devices and users including automatic detection for ultimate scaling and growth.
Monitoring
Continuous monitoring of sensitive data for regulatory compliance, data governance and data loss protection.
Prioritization
Effective prioritization of security incidents to significantly reduce alert fatigue and burnout, and ensure timely response.
Automation
Automatic handling of 95% of security tickets, freeing up lean IT teams and optimizing resource management.
AI capabilities
AI-powered detection, analysis, prioritization and remediation across all modules.
Single touchpoint
Curated threat intelligence and logs served up via our unified interface.
Recommended products
The First Modular Approach that Covers all your Security Needs
Coro monitors network access and user activity on cloud apps, email, and endpoint devices to ensure the protection of regulatory-sensitive data and business-sensitive data based on your unique business requirements.
Data governance & data loss
- Monitoring sensitive data on endpoints, email, & cloud drives
- Encryption of endpoint drives
- AI-driven detection of data that deviates from a predefined pattern
- Data monitoring logs for a compliance audit
Malware & ransomware protection
- Detection and remediation of malware and ransomware in email attachments
- Anti-virus (AV) for signature-based detection and remediation of files with high-risk content
- Detection and remediation of malware and ransomware files in cloud drives
Phishing & human error protection
- Unlimited allow and blocklisting for individual senders, email domains and email servers
- Social graph-based analysis of user/domain spoofing and impersonation of individual employees
- AI-driven phishing detection
- Real-time, automatic remediation of suspicious emails
- Detects links to untrusted entities
User account attack and compromise
- Real-time, automatic remediation of unauthorized access
- Data-driven anomaly detection, aware of your entire organization and individual end-user behaviors
- Security monitoring with geo and network fencing for cloud app access (Microsoft 365, Google Workspace, Salesforce)
Dangers of remote and distributed work environments
- Secure Web Gateway (SWG) with advanced content filtering
- Firewall-as-a-service
- Zero Trust Network Access (ZTNA)
- Split tunning VPN with enterprise-grade encryption support on Windows, macOS, Linux, iOS & Android
- Virtually impenetrable cloud network that monitors and controls networking of internal and cloud resources
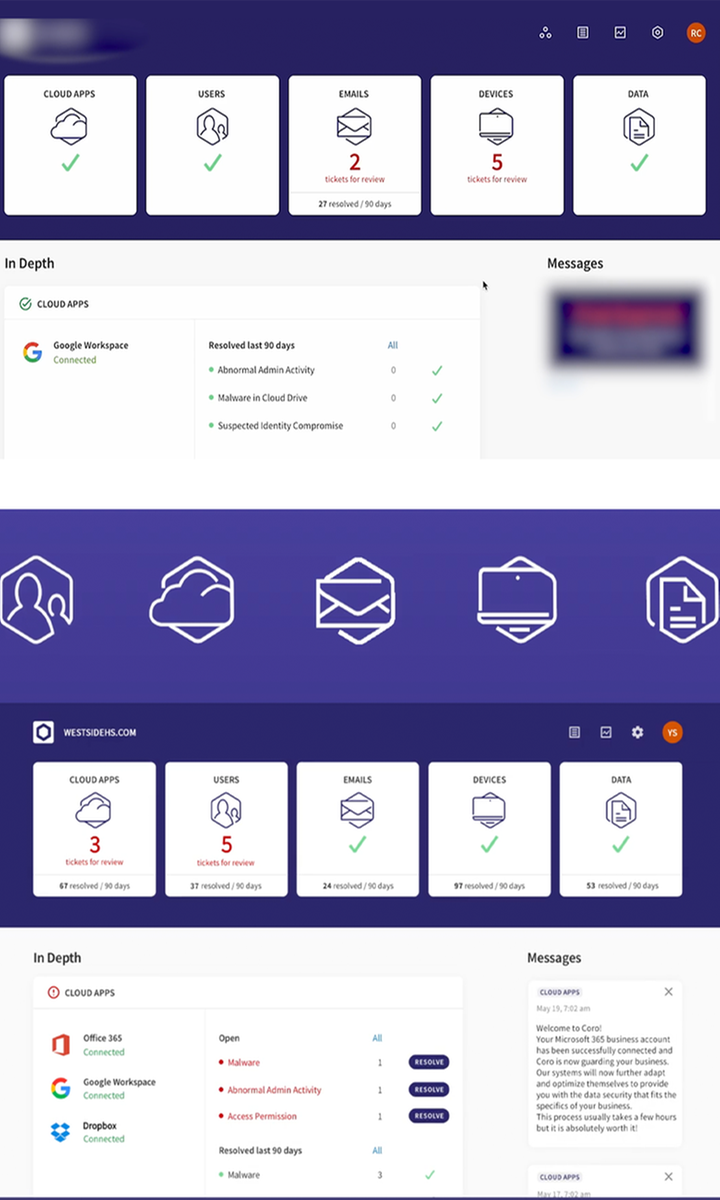
Additional Information
Terms & Conditions
Terms of Service
https://www.coro.net/termsPrivacy Policy
https://www.coro.net/privacyResources
Coro 3.0 Modular Cybersecurity - Datasheet
Powered by WHMCompleteSolution